
Part 1 – Introduction
This will be a multi-part post about recent developments that should be of concern for serious digital marketers. In particular, large digital advertisers that use Adobe Analytics (or other non-Big G Analytics platforms) and whose media agencies (or internal digital media buying teams) also use Big G Ads/Search/AdWords beware.
The Problem
Apple’s most recent Safari release in September 2018, which effectively blocked all 3rd party tracking cookies is being blamed for what amounts to a clandestine behavioral data land grab by Big G. In going along with this charade, digital marketers everywhere risk the de facto relinquishment of digital measurement and customer behavioral data to others with different and not non-transparent interests that create a competitive disadvantage.
Through major brands’ own media agencies, Big G has been cannily pushing everyone to use a new kind of Web site tracking tag that circumvents Safari’s strict privacy features. The new code snippet replaces the legacy DoubleClick Floodlight tags that have been historically appended the brand’s destination Web site on key actions, e.g. order thank you page. The loading of that page and associated 3rd party tags signal a successful “conversion” event for analytics and ad targeting optimization purposes.

Floodlight 101
The DoubleClick Floodlight tag was created as an adjunct to the agency ad server (a/k/a 3rd party ad server) which was initially developed to enable ad impression delivery in the user’s browser to be associated with later events on the advertiser’s Web sites. In this way, a kind of campaign measurement could be performed showing cause (ad delivery) and effect (purchase event). However, the method relies a 3rd party cookie from doubleclick.net set at time of ad delivery to be safe and secure in the user’s browser and recognized by the Floodlight tag when the user subsequently interacts on the advertiser Web site.
Additionally, the Floodlight tag has the capability to piggyback other tags from media vendors like ad networks so that they could also measure and optimize their campaigns in flight based on actual performance, e.g. order confirmation pages firing. Similarly, ad analytics uses include brand lift studies and multi-touch attribution. Not surprisingly, over the years Big G has shoved more and more back-end server-side functionality into the Floodlight tag to help their other businesses like AdWords, Bid Manager and Dynamic Creative Optimization.
The problem with the new code snippet is that the tag is no longer the kludgey Floodlight but the much more powerful Big G tag manager. The latter was engineered to sending data back to Big G faking 1st party even though it is not really (similar to Big G Analytics). Compounding the challenge for digital marketers is the aggressive recommendation to install the new GTM code snippet onto *all Web site pages* instead of just swapping out existing Floodlight tags.
The Bait and Switch
Within the new code snippet itself, note that the comment text still says “DoubleClick” but the actual server being called is not doubleclick.net anymore but is googletagmanager.com. Big G’s timing of the recent name change dropping the DoubleClick brand from everything is interesting and has further caused confusion with the site operations and ad operations team that work with these technologies.
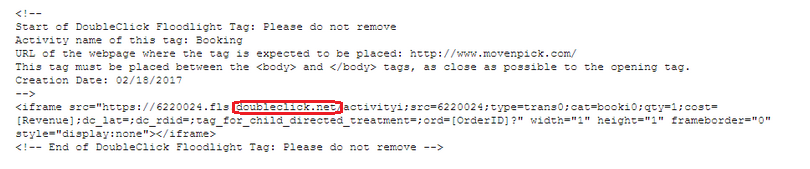
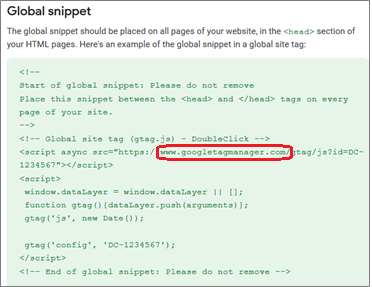
Major digital advertisers that are not already using Big G Analytics/Tag Manager are particularly susceptible to the false sense of urgency in this crafty switcheroo. Especially those from industries with limited digital competency. In the end, Big G gets better clickthrough conversion tracking for search and client-owned Web site analytics platforms like Adobe Analytics, Webtrends, IBM Digital Analytics or Matomo remain as is.
Clients should consider pushing back on what amounts to a digital behavioral data cookie grab.
COMING UP: Part II – Victim-blaming with Apple ITP.